VPN vs. proxy server: What’s the difference?
In the digital era, where Big Data is the most valuable resource of the 21st century, it’s necessary to protect your virtual identity. There are different methods for doing so, but the most common is using a VPN or a proxy server.
On the surface, they seem to be very similar. For example, both solutions hide your IP address so that no one can trace it. Each one acts as a middleman: you establish a connection with a proxy or VPN server, and then that connection forwards your request to a website. So to the website, it looks like you're connecting from the server, and they don't know anything about your real location. But that's where the similarities end. VPNs and proxies offer different levels of security and privacy and support different protocols.
What is a proxy server?
The definition of the word "proxy" means a person who is authorized to act for another, and a proxy server acts on behalf of the user. All user requests first go to a proxy server, which evaluates the request and forwards it to the Internet. Similarly, replies are sent back to the proxy server and then to the user. In this case, the user's computer does not communicate with web services or websites directly, this is performed by a proxy server, which applies as a middleman.
Modern proxy servers also can also operate as web filters and firewalls and protect network resources. Reverse proxies are used by service providers to improve website performance (by using caching) and balance load between servers.
Proxy types
Proxies aren't all the same. There are different protocols that a proxy could use, depending on the type of application you're using, and they offer different levels of security.
Transparent proxy
Transparent proxies do not hide any user-identifying information. They send a request to a web server, and it’s shown as coming directly from the user.
Transparent proxies are set up by the network operator, not by the user, and are typically used for:
- Filtering content. With transparent proxies organizations might block access to content that is not relevant to employers' work, for example, social media platforms. Libraries and different public organizations might use transparent proxies for the same purpose.
- Monitoring activity. Transparent proxies can also be used for logging the online activity of the users inside the network and tracking visited websites.
- Caching. The transparent proxy server checks outgoing traffic and if the requested content is present in the cache, the proxy server returns it to the client without contacting the remote server. This option helped a lot in saving bandwidth and improving Internet connection speed, but the widespread use of HTTPS makes it lose its relevance.
Also, the term ‘transparent proxy’ is used to denote a remote proxy server, which redirects requests, and, for example, can help to unblock access to websites. But in this case, the user’s online activity is not anonymous because his/her real IP address is transmitted in the X-Forwarded-For (XFX), Forwarded or X-Real-IP headers.
Anonymous proxy
An anonymous proxy server, or the anonymizer, is the opposite of a transparent proxy server. When you browse the Internet with an anonymous proxy, all your traffic goes through the proxy server, which strips away your IP address. It gives users following benefits:
- Online activity is harder to monitor.
- Geoblocking cannot rely on your IP, because an anonymous proxy doesn’t pass it.
Anonymous proxies can be unsafe and may collect and sell users data. If you don’t want to put yourself at risk, buy a proxy service from a trustworthy provider.
Forward proxy
The client asks its internal network server to forward a request to the internet. Forwarding proxies are configured to allow or deny a user's request to access web content through the firewall. If the proxy allows the user's request, it forwards the request to the web server through the firewall. The web server sends a response to the proxy server. The proxy server then sends this response back to the user.
Reverse proxy
A reverse proxy, in contrast to forward proxy, is placed between clients and origin servers. This type of proxy accepts requests from clients and sends them to some server behind it. The response from the server returns to the client through the reverse proxy, making it appear as if the proxy server handled the request itself.
Here are some benefits of using reverse proxy:
- Load balancing. Reverse proxies are able to distribute incoming traffic across servers in a network so that servers’ resources are not depleted.
- Security. Reverse proxies can be used for monitoring suspicious activity, preventing data breach and DDoS attacks, and controlling unexpected traffic spikes.
- Optimized content delivery. A reverse proxy can compress outgoing files, cash content and improve website performance.
HTTP proxy
HTTP is the web protocol used for transmitting data over the Internet, mainly between web browsers and servers.
Some of HTTP proxies only support GET/POST requests and don’t support encrypted connections (HTTPS). Now such proxies are practically useless, since most of the web traffic is transmitted via HTTPS. In addition, using these proxies is dangerous, because the proxy owner can read and even modify transmitted data. Previously, such proxy servers were often used to inject advertising or malicious code.
There are also HTTP proxies that support encrypted connections through the CONNECT method and can be used to consume HTTPS content. In this case, the owner of the proxy only can see the domain name of the website you are accessing, all other data is encrypted. Also, this type of proxy can be used to hide your real IP address from the website owner. But it doesn't work if you want to cover your IP address from your ISP or the government, to hide the domain name of the website you visit, and to bypass censorship.
Secure proxy
This kind of proxy got browser support in the 2010s. Based on HTTP, it was enhanced by TLS cryptographic protocol and SSL certificate, enabling secure encrypted connections to be set between a client and a proxy. This solution is close to a VPN by the level of privacy. It guarantees strong protection of transferred data and hides from your ISP the domain names of the websites you visit. This technology is used by VPN extensions for Chrome, Firefox, Edge, and other browsers.
SOCKS proxy
SOCKS (SOCKets Secure) is a modern proxy technology used to transmit data packets between servers and clients.The latest version of protocol is SOCKS5. It routes user traffic through a third-party server — the SOCKS proxy — via TCP (Transmission Control Protocol) or UDP (User Datagram Protocol). You can use it only when an application supports it. This could be music, streaming, voice chat, games, or anything media-related. SOCKS proxy effectively hides the user’s IP address but doesn’t encrypt the user’s data.
Is it safe to use a proxy?
Prior to HTTPS free public proxies were widely used for ad injection, credentials stealing and even for browser exploit injection, for example installing viruses on clients’ computers. Nowadays, when almost all web traffic is encrypted, it's impossible or at least harder to abuse the technology. However, owners of proxy servers still have access to users’ browsing history and can collect it for their own purposes.
Also, it's important to remember that proxies do not protect you from firewalls or ISP spying, because the domain names of websites you visit are transmitted as plain text. In addition to all the above, if an operating system or web browser is configured incorrectly, your real IP can be revealed through DNS leak. This applies not only to proxies, but to VPNs and socks proxies as well.
How does a proxy server work?
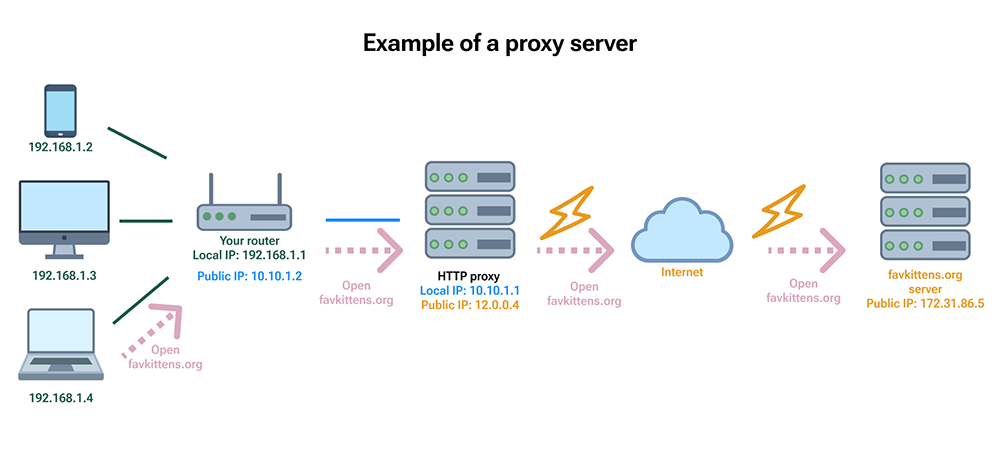
As we already know every device connected to the web needs an IP address, which is used to deliver data from the server back to the client. It’s helpful to think about IP as an actual address, which reveals information from where every user is connected to the web. Based on information about the user's IP address, different websites or web services might block access to their content.
Proxy server is an intermediary computer that has its own IP address. When a user connects to a proxy server, all web traffic is rerouted through it and the user's IP changes to the server's IP.
A proxy server can be set up as a common ‘exit point’ to provide clients and networks access to the Internet. Also, it can be configured as an ‘entry point’ to a network behind it.
What is a VPN?
VPN (Virtual Private Network) is a program that establishes a secure network connection over public networks. A VPN encrypts internet traffic and hides your identity online. This makes it harder for third parties to track your online activity and steal your data. Encryption happens in real-time.
How does a VPN work?
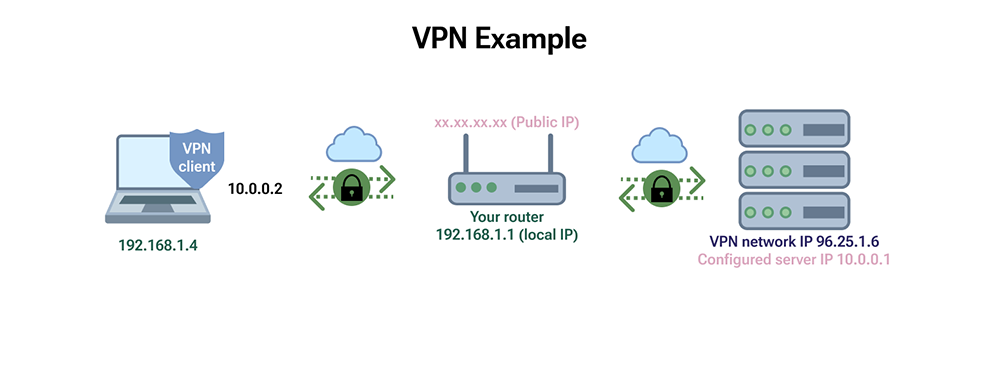
A VPN hides your IP address by allowing the network to route it through a specially configured remote server controlled by the VPN host. This means that if you browse the Internet using a VPN, the VPN server becomes the source of your data. Your ISP (Internet Service Provider) and other third parties cannot see what websites you visit or what data you send and receive over the Internet. The VPN acts as a filter that turns all your data into "gibberish." Even if someone managed to get hold of it, it would be useless.
VPN vs. proxy: key similarities
There are key similarities between VPNs and proxies.
- They both add an extra layer of protection when you use the internet by redirecting your information to a secure third party, rather than allowing a direct internet connection to your computer or a protected network.
- They both hide your user IP address, so you can remain anonymous on the internet.
- In both cases, whether it’s a proxy or a VPN, traffic travels longer distances and makes more network hops. That slows down connection speed to some extent (it may be almost unnoticeable or quite disasterful, especially if a proxy/VPN server shapes traffic, i.e. has some bandwidth limits per client set).
VPN vs. proxy server: key differences
There are some fundamental differences between a VPN vs. proxy server that many people don't realize.
Technical differences
From a technical perspective, VPNs and proxies work on different levels of a network abstraction model. Proxies live on the L7 level of OSI model – application level. VPNs, on other hand, operate on L3 (network level) or L4 (transport level). To put it simpler, proxies work with requests of a specific type (HTTP requests, if we talk about HTTP proxies) and VPNs work with network packets of data.
Accessibility
VPNs are configured at the operating-system level so in the simplest case all traffic goes through the VPN’s encrypted connection. It can be used with any traffic or any type of app, so you can use a VPN while you're playing a game, streaming music, or sharing files. Some VPN services allow you to exclude certain websites and apps.
A proxy server, on the other hand, is usually configured at the individual app level. You have to go into your software’s settings and put in the proxy connection settings; then, it would be used only within that software, and everything else will be unaffected. Basically, only the traffic originated by web browsers gets rerouted.
Security
The next major difference has to do with security. In general, VPNs are more secure than proxies. All VPNs work similarly: they encrypt data, put it in the tunnel, and send it to a VPN server. For encryption, VPNs use protocols that may differ, as well as the level of protection provided. Today, the highest encryption standard is AES-256.
Now, if you really wanted to, you could set up your own VPN server and configure it to not use encryption. But if you’re using consumer VPN software (which main goal is privacy), it likely won’t have the option to disable encryption.
Encryption
VPNs commonly encrypt all your internet activity, while a proxy does not. Encryption ensures that no one can access your online activities and sensitive data. So, a VPN protects you from the prying eyes of hackers and ISPs.
VPN vs. proxy: What to choose?
Proxy, as well as VPN, masks your IP address. But if you want to reach more in anonymity and security, while using a wide variety of apps, VPN is the way to go. VPN in contrast to proxy uses encryption to make your online traffic completely unreadable for an ISP or a government. When you use a proxy, they are still able to monitor your online activity. Moreover, VPN allows you to hide the fact of using a VPN, but proxy does not. So that with VPN you can use the internet without being tracked.
High-quality VPNs as well as proxies can’t be free, so it’s better to stay away from services, which don’t charge users and cover costs in other ways. For example, a proxy server that relies on advertising revenue can share your data with third-party networks. In addition, proxy servers can be used for black-hat purposes. Hackers can set up a "free" proxy server to gain access to websites or infect clients’ devices.
This makes VPNs much more secure and efficient.
Why choose AdGuard VPN?
As promised, let’s discuss VPN services with AdGuard as an example. Here is the list of special features:
- Proprietary protocol. AdGuard VPN’s protocol is built from scratch rather than using an off-the-shelf solution.
- Exclusion lists. Users can choose how to use the VPN: on all websites and in all apps except those added to exclusions, or vice versa.
- Choosing a DNS server. You can choose DNS servers from the list or even set up your own one. There is really no need to rely on your ISP.
- Fastest locations. You can choose which country you want to surf from, there are more than 50 locations available. Also, you can see the ping to each country.
- Compatibility with AdGuard Ad Blocker. AdGuard VPN works well with our ad-blocking program, both on desktop and mobile devices.
- QUIC support (experimental). QUIC is a protocol that helps when you have a poor internet connection.
- Kill Switch. A bulletproof method for situations when your VPN connection is interrupted. Kill Switch will automatically disconnect the internet connection.
- Auto-protection. When connecting to any public WiFi spots, you’ll be automatically connected to AdGuard VPN.
- Simultaneous connection allowance. Some VPN service providers allow up to five devices to connect to their services. With AdGuard VPN, there is no limit to the number of devices that can connect to your account, but you can have five VPN connections enabled at the same time.
- Secure streaming. Hard-to-detect VPN “activity” helps you hide your media streaming.
Try AdGuard VPN! Download it on your macOS or Windows, iOS or Android device, or install a browser extension for Chrome, Firefox, Edge, or another browser to fully control your online activity and data security.
FAQ
Is a VPN better than a proxy?
It really depends on what you want to achieve. If you just want to increase your online security, a VPN will usually be a better choice. However, if you just need to change your IP, or for example, programmatically scrape something from a website without seeing 429 errors, proxy servers will be much better suited for that.
Do you need a proxy if you have a VPN?
There are no technical reasons preventing you from using a proxy on top of a VPN. On the other hand, if you already have a VPN installed, there are not so many reasons why you might need to do that. Scraping something on the web, when you simultaneously need to use lots of IP addresses, is among a small number of those ‘special’ reasons.
Are proxies free?
No, not all proxies are free, but it’s not a problem to find a free one. However, trustworthy, high-quality developed proxy service can’t be free. If you don’t want to put your privacy and anonymity at risk, stay away from free proxies services.
Does a proxy change your IP?
Yes, that’s one of the reasons to use a proxy. Remember that when we talk about "changing" an IP address, we are essentially talking about masking it.
Do proxies hide your IP?
Yes, proxies hide your IP address. However, the proper term for it would be “masking.”
Can I be tracked if my VPN disconnects when I use it?
Yes, you can be tracked, because all your data becomes revealed. Premium service providers enhanced their VPNs with a kill-switch feature, which cuts off your device from the Internet if the VPN connection is lost.
Which is faster, a proxy or a VPN?
Proxy as well as VPN slow down Internet connection speed. The reason is that transmitted data has to pass a longer way to reach a VPN or proxy server first. It can be almost unnoticeable if you are a premium user, have good Internet and connect to a nearby server, or a bit annoying when your Internet connection isn’t good enough and you choose a distant VPN server.